 |
|
YES SECURE NETWORK
Secure connectivity for Apple® iPAD ™ and iPHONE ™ users
|
|
|
| 1. Introduction YES Secure Networks |
|
1.1 Profile
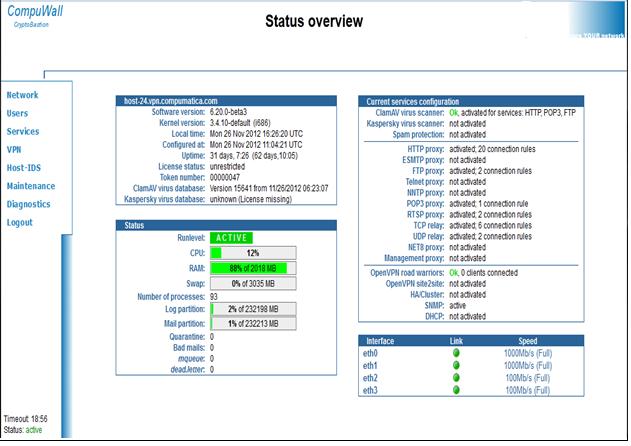
YES SECURE networks is a team of 45 highly skilled, qualified and motivated staff members develops high-quality security solutions for the protection of confidential data over public or private networks. We develop, produce and implement crypto systems for organizations with the highest security requirements such as governments, banks, insurance companies, industrial companies, media. |
|
1.2 Vision
Cyber crime by spyware, viruses, hackers and botnets is growing fast in size as well as in intelligence. These threats no longer focus solely on fixed connections, but more and more on the mobile domain, causing much harm and damage to business and unsuspecting users. Securing access to data plays an increasingly important role. It requires knowledge of secure access via fixed and mobile networks and policy development around it. |
|
1.3 Mission
"The security of your data is our job - we secure YOUR network." To this basic idea, we feel obliged from the start. For your specific requirements, we develop complex security solutions. YES Secure networks also works closely with the governments and has regular consultations on current and future security demands. Based on YES Secure network knowledge of the market trends we respond quickly to new trends and assess their value. This enables us to provide our customers with sound advice to support them in finding the appropriate measures to ensure that data remains safe and yet accessible for employees anywhere in the world for any appliance whatsoever.
New and on-going developments of our solutions focus on the needs and requirements of our customers. The experience of professionals is integrated in the development to make the products even easier to use. The trends in the market, the potential risks, the knowledge of our developers and market researchers from YES Secure network form our road map.
Strategic objective in 3 to 5 years
As one of the provider of international crypto solutions we work continuously on improving our products and processes in order to strengthen our position, to increase the trust of our existing customers and to gain new customers. By applying "innovation", we help our clients to find new security solutions for the secure use of smartphones and tablets for business purposes. Together with our customers we develop these new applications in a way that enables them to fit easily into existing processes and procedures, that reduces management effort, and if procurable to get them approved for governmental for certain classifications. YES Secure network wants to reach a top position in the BYOD market, like we did for our other products and services by delivering optimal security for a reasonable and fair price. |
| |
2. What is the problem?
|
|
People want to be flexible, highly mobile, and want to stay “connected” at any time and wherever they are.
Companies see big advantage in the use of mobile apps and want to implement these in their processes.
|
|
|
Question ?
How to comply with security standards !!
|
|
 |
|
|
Situation mobile users
|
|
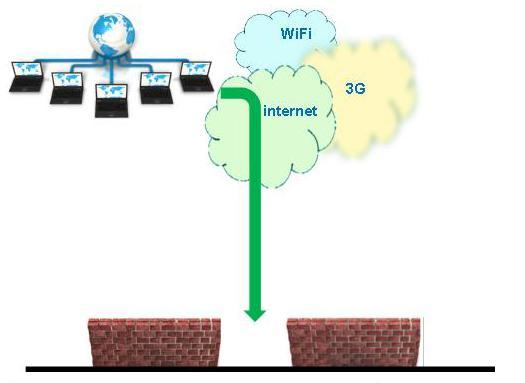
Mobile users are somewhere “in the cloud”
|
|
 |
|
 |
|
Most Companies already have policies to connect laptops to the companies data.
|
|
| |
|
Situation mobile users
|
 |
|
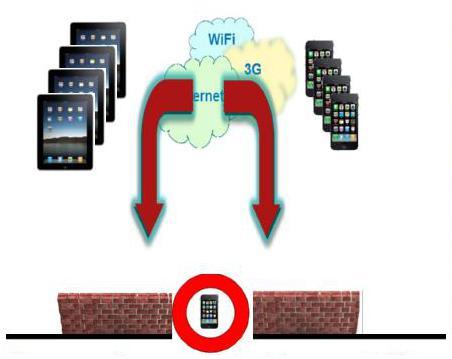
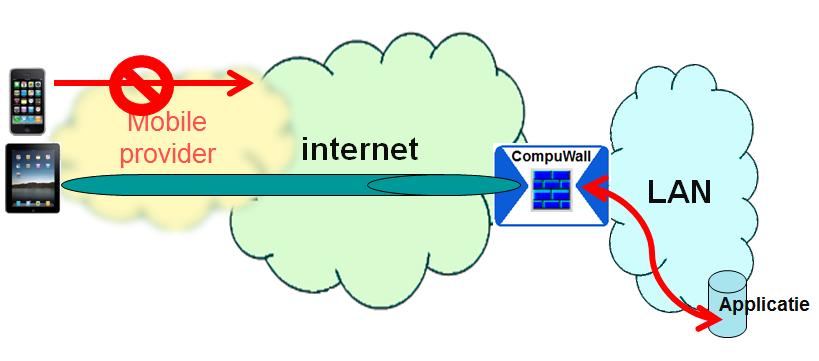
Company policy prevents smartphones and tablets to connect to the companies data.
|
 |
|
|
|
Solution
|
|
The solution is based on the YES Secure CompuWall Firewall / Bastionwall / VPN-concentrator which is approved by the Dutch Government for “Departementaal Vertrouwelijk” ( and NATO Restricted) .
|
 |
|
|
Tasks of the CompuWall
|
|
|
- As a Firewall: Guardian for the connections between the different networks
- Stop all traffic that’s not allowed
- Inspect / filter all traffic that’s allowed
- As a VPN-concentrator: Build and maintain secure tunnels
- Laptop, Android and Windows mobile can make use of the OpenVPN client
- iPhone/iPad can make use of built-in IPsec
|
|
|
|
3. Solution description
|
2.1 Introduction
In response to requests from our customers to securely connect their smartphones and tablets to their Centralize IT resources, YES Secure network investigated the possibilities to use existing solutions of our portfolio and our knowledge of securing remote connections to fulfill these requests. The demand for security connections for Apple’s ® iPhone ™ and iPad ™ was the most concrete and urgent one making us focus on solutions focused on the Apple® iOS devices. YES Secure network will use a phased approach as we recognize several stages that need to be completed and that are explained and described further on in this presentation. |
|
2.2 Solution components
By making use of YES Secure network’s existing application layer firewall named CompuWall, as the VPN concentrator we can setup the needed crypto tunnels to the devices. The CompuWall is a highly reliable Firewall and already approved for government restricted use. The CompuWall uses Certificates, either generated by the CompuWall or by other devices. The tunnel protocols are based on IPsec as IPsec is standard available in Apple© iOS. The encryption is based on AES256. By making use of policies, the device is isolated from direct access to the Internet (Wallet Garden) and all communication is forced by the tunnel to the own IT environment where a customer can create an AppStore for applications, or where, like Dropbox, files can be stored and retrieved. In order to manage these clients, customers can make use of a so-called MDM solution (Mobile Device management) with or without a Self-service portal. YES Secure network will not directly deliver AppStores, MDM solutions and virtual storage solutions. |
|
2.3 Phased approach
YES Secure network takes a phased approach in order to be able to bring solutions faster to the market and to avoid unnecessary complexity. The first phase consists of the CompuWall/VPN concentrator responsible for setting up, based on IPsec, the secure tunnel to the mobile device. We make use of the certificates generated by the CompuWall and push them, by means of a script, to the mobile devices. |
|
|
|
2.4 Deliverables of phase 1
The deliverables of phase 1, the phase aimed at realizing Proof-of-Concepts, testing purposes, quick scans and later on for approval by certification authorities, are:
- Acceptation of the certificate and the roll-out of the script (i.e. the policy) to the mobile device.
- Construction of the IPsec VPN tunnel by making use of the standard Cisco VPN-client that is part of Apple’s ® IOS. The VPN tunnel is in this stage terminated on a Linux server that resides behind the server with the CompuWall installed on it. In phase to the development, code will be integrated in the code of the CompuWall. A user interface will also be added in stage 2 in order to support the management of VPNs.
- Encapsulation of the mobile device (Walled garden) to prevent direct communication with the mobile device via Internet by creating a secure tunnel.
- Proxy implemented in order to provide controlled access to data/applications on servers behind the CompuWall. Controlled access means that you allow or disallow mobile access certain access to applications and/or data.
The drawings below illustrate the various stages. |
 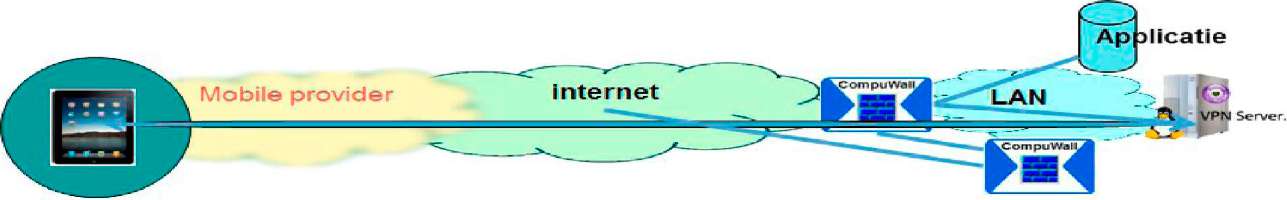 |
| Drawing 1: The mobile device solicits for connection to the data /application environment on the LAN using the IP address / URL of the IP address / URL of the router/CompuWall. This address should be manually entered on the mobile device (Settings/Network settings). This can be realized by making use of 3G as well as when connected to the Internet via Wi-Fi, Hotspot etc. |
 |
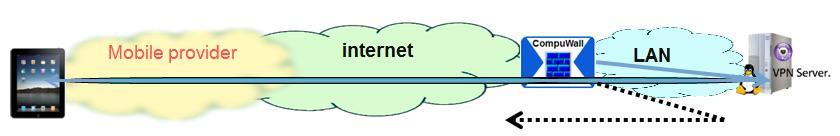
| Drawing 2: CompuWall checks authentication of the mobile device that wants to connect and matches it with the user list. |
|
|
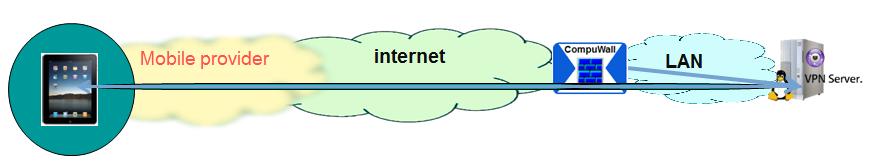
| Drawing 3: The certificate, generated by the CompuWall and pushed to the mobile device needs to be “trusted “by the mobile device. As soon as it has been trusted, the tunnel is opened for bi-directional communication. The policy is hardened on the mobile device. |
|
|
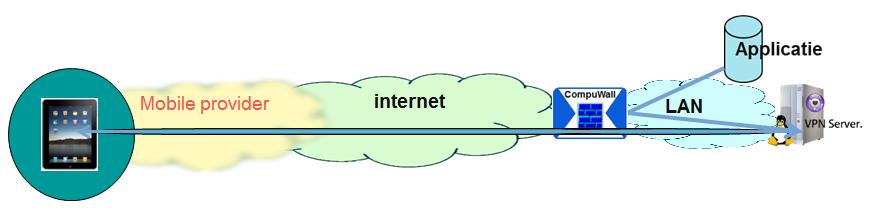
| Drawing 4: Part of the policy is the “Walled Garden”, that blocks the direct access of the mobile device to the Internet. |
|
|
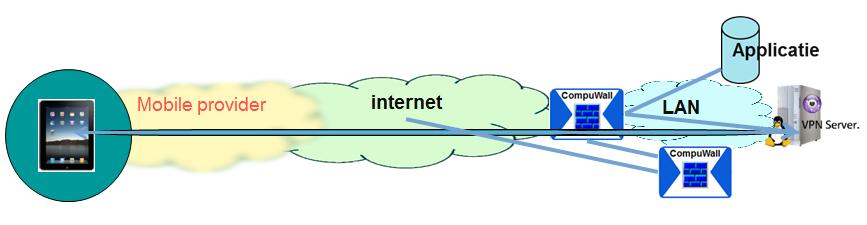
| Drawing 5: By means of the pushed Apps to the mobile device the access to data and applications residing on the LAN is enabled. |
|
|
| Drawing 6: Via the LAN a link to the Internet can be established via the Firewall. By making use of a white list, access to certain web environments can be controlled and assigned to the mobile clients. This is an option to phase 1. |
| |
|
4. Next Phases and continued developments
|
4.1 VPN addition to the CompuWall
The YES Secure network CompuWall as it is right now supports OpenVPN. Apple® iOS as it is right now supports IPsec as VPN implementation but not OpenVPN. To bring both worlds together, YES Secure network will add IPsec as VPN implementation to the code of the CompuWall, like it will add the OpenVPN implementation that has been certified as restricted by the government certification authority NBV. This will support future development with respect to secure communications with Android ™ and Windows 8 ™ based mobile devices. |
|
4.2 Hardware based encryption
The basis for this stage is YES Secure network’s encryption solution for secure voice and text messaging as certified as restricted for the use in BlackBerries and makes use of a MicroSD card. This card is the center for executing and storing all cryptographic functions and keys, like encrypted settings, address book, the store for text messages. The card itself is protected by a PIN-code. This solution will be used and adjusted so that iPhone and iPad users can make use of this solution, too. YES Secure network will develop a solution based on a MicroSD card reader, connected by means of Bluetooth ® with iOS. Additional benefit of this solution is that in case the mobile device is taken from its owner/user, the connection will be broken and the device can no longer be used. |
|
4.3 Further developments
The focus will be on certification and connecting other mobile platforms like Android ® and Windows 8®. |
|
|
|
|
| Back to YES Secure Networks View YES Secure CompuWall |
|
|