|
 |
|
YES Secure - Security Management Station
|
|
Enhancing your security management. The centralized security management approach.
|
|
|
|
Network Security plays an important role for any company's IT management. For a better protected environment, security components have to be integrated into the firm network. A central security management station that is both effective and simple in use can fulfill these security demands.
|
|
|
|
|
|
Network Security today ranks high on the list of any company's concerns. Almost all of a firm's relevant information is exchanged in electronic form via networks. Since the network technology employed by a company may assist attackers in many ways, these networks do not generally guarantee security or confidentiality for a company.
For this reason, security has to be added to the firm networks. The corporate security manager can fulfill the pure security requirement by integrating additional security devices into the existing network, whereby the management of these devices is an important consideration. A central, easy-to-handle management station is a main prerequisite to fulfill the security requirements.
Concerning the management of security components the corporate security manager generally has the choice between two different approaches. The first one is the local management approach. The idea behind local management is that the corporate security manager can manage each component individually, thus he has the highest flexibility with control over each flag in the components. The second approach is the security management approach, in which the idea is that the corporate security manager has a higher-level overview of the whole system and does not have to spend too much time with component details.
Both approaches have their pros and cons. The security management approach, however, offers the following advantages:
- in general, a company wants or has to use a VPN system as an additional mechanism,
- the handling of the mechanism will be as easy as possible,
- the results are secure and understandable for the company staff.
|
|
|
|
The YES Secure Networks Solution: The security management station (sms)
The Security Management Station (SMS) is such a tool to realize central and connection-oriented security management. It follows the centralized management approach and gives a high-level overview of the entire security system within a company. It handles all details automatically in the background. However, the corporate security manager can still examine and analyze details of the security devices. This is also possible for each security device of the YES Secure CryptoGuard VPN system.
|
|
|
|
The CryptoGuard VPN Product Line
The SMS is part of the YES Secure CryptoGuard VPN and YES Secure CryptoWall security system, which additionally contains the CryptoGuard VPN device and the CryptoGuard VPN Client. Furthermore, the SMS can also manage the CryptoBastion, an application level gateway. All information about a company's VPN system (e.g., the specific security devices and security policies) and about the network in general (e.g. network nodes, gateways and connections) is stored in the database of the SMS. The security-relevant information (e.g., master or system keys) is stored encrypted, making it impossible to extract them from the database in a readable form.
If the corporate security manager combines the two security systems CryptoGuard VPN and CryptoBastion under one management system he will be able to create powerful network security solutions for his company.
|
|
|
|
|
|
|
|
|
|
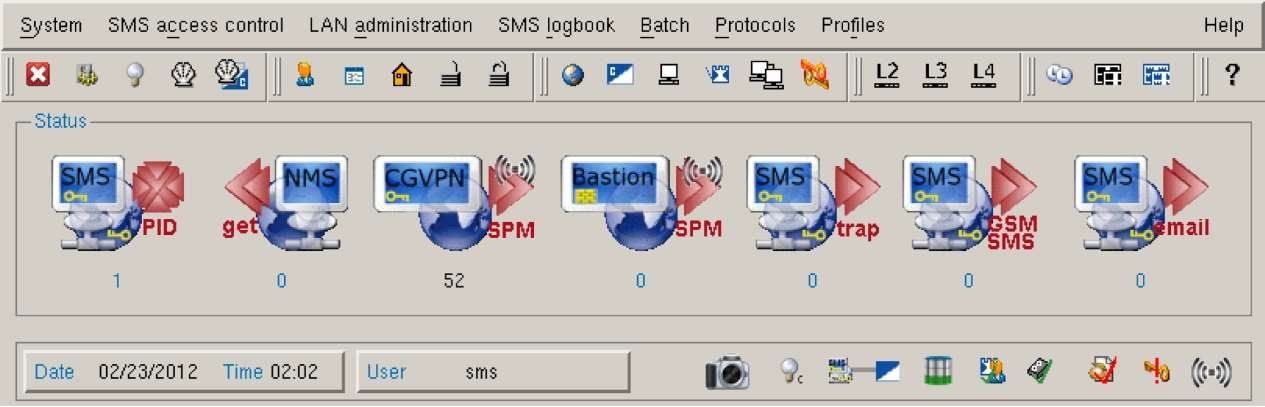
The Security Management Station (SMS) enables the central administration of the different CryptoGuard VPN devices and the firewall element CryptoBastion with numerous and comfortable options. With the SMS, filter rules are defined and all cryptographically secured connections between the CryptoGuard VPNs are controlled (the SMS e.g. receives alarm and status messages of the VPN components).
|
|
 |
|
The SMS furthermore provides a sophisticated key management and various options to create Virtual Private Networks. The communication of the Security Management Station with CryptoGuard VPN and CryptoBastion is encrypted – thus eliminating a common target for attacks at firewall systems.
The SMS can be easily integrated into the existing network and, if necessary, maintained remotely from any place in the world in a secured way.
A clear graphical network topology reflects the actual network structure at any time and enables the systematic distribution of the generated rules to the corresponding components of the security system. Predefined protocol profiles can help facilitate the use of applications and the creation of sets of rules. By means of the integrated management of roles, mechanisms such as the four-eye principle can be realized.
|
|
|
|
Key features and benefits
Easy integration into existing network topology
- CG VPN black box principle
- SMS integration as a single network component
Backup/Restore mechanism
- The Backup includes the configuration data of the whole security system, that means for all CryptoGuards and all CryptoBastions
Secured communication between SMS and security components
- Proprietary authentication protocol based on ITSEC E3/high certified method
- Customer specific S-boxes are loadable
Downward compatible to the beginning
- Reliable compatibility to CryptoGuards and CryptoBastions of the first generation with a history of about 10 years
Easy definition of secured connections
- After creation of topology no knowledge of security components necessary
- Just connection endpoints and security policy necessary
- Support of templates by using service/protocol/time profiles to simplify the creation of the security policy
- Simple method of enabling/disabling of connections and protocol profiles
- As connection mode the proprietary CG VPN mode and IPsec are available
- Interdomain communication by using shared key material
- Automatical generation of configuration files for CryptoGuards and CryptoBastions
- According to the Compumatica VPN security policy:
- All is forbidden except for the explicitly allowed connections
Logging functionality
- Logging of tasks performed at SMS (functions, errors, login/logout) as preservation of evidence
Excellent key management
- Automatic generation of connection key files used by CryptoGuards
- Exchange of connection keys: Beside the key management mode IKEv1 also IKEv2 is supported within IPsec
- Beside the authentication method RSA also ECDSA (Elliptic Curve Digital Signature Algorithm) is supported within IPsec and IKEv2
- Generation of CG VPN mode keys ((A)DES, 3DES, AES)
- Generation of IPsec keys (MD5, SHA-1, DES, 3DES, BLOWFISH, CAST-128, AES, ...)
- RA/CA/PKI included to generate X509v3 certificates e.g. for using in IPsec connections with RSA signatures as authentication method
- PKI:
- Beside RSA also ECDSA certificates are supported
- Support of proprietary elliptical curves (EC)
- Distribution of the CRL to several LDAP servers
- Mark CA certificates as "Trusted", "Not trusted" and "OCSP"
- Mark certificates near the expiration date
- Import of PKCS#12 (Certificate and Private Key container)
- Smartcard functionality
Centralized security management
- Centralized point of security management and single point of trust
- Automatically and centralized configuration of CryptoGuards and CryptoBastions
- According to the Compumatica VPN security policy:
- CryptoGuards and CryptoWalls are managed by the push method
GUI based security management
- Ergonomic design
- Visualization of network topology as initial point of the management
- Visualization of connections and all the security devices involved
- Powerful search functionality by user defined criteria
- Multi language support: Currently English and German are available, other language implementation upon request
- Print functionality
- HTML based Online Help
SMS owned user access control and role administration
- Application based user access control
- Administration of organizational units
- User roles to split responsibilities
Centralized and user-friendly management of CryptoGuards
- Configuration by means of dividing generation, transmission and activation of configuration files
- Certificate Signing Request (CSR)
- Certificate revocation status determination using OCSP
- Certificate Revocation Lists (CRLs)
- Perform Integrity check
- Retrieving and visualization of statistic information
- View SA list in case of IPsec
- Perform Selftest
- Get Log book
- Exchange of connection keys: Beside the key management mode IKEv1 also IKEv2 is supported within IPsec
- Software upload
- White list of version check concerning software upload
- Import/Export of certificates
- ...
Centralized and user-friendly management of CryptoBastions
- Configuration (General, Proxies, ...) by means of dividing generation and transmission of configuration files
- Perform Integrity check
- Select operation mode (Runlevel)
- Get Log book
- Retrieving and visualization of statistic information
- ...
Centralized and user-friendly administration of network components
- Single network component, Server, IPsec Client, network
- Import/Export of network components
Alert functionality
- Reception of spontaneous messages of CryptoGuards and CryptoWalls and storage in database
- Forwarding of spontaneous messages of CryptoGuards and CryptoWalls as SNMP-Trap, E-Mail or GSM-SMS
SNMP interface
- SMS acts as SNMP proxy agent
- Support of SNMPv3
- SNMP-Trap
- SNMP-Get (Status, Selftest, Statistic, Ping (Echo Request), Version, …)
- MIB available
Administration of batch orders
- CryptoGuard
- Exchange of connection keys: Beside the key management mode IKEv1 also IKEv2 is supported within IPsec
- Time synchronization between SMS and CryptoGuard
- Software upload
- Get Log book
- CryptoBastion
- Get Log book
- Integrity check
- SMS
Redundancy mechanism
- Active redundancy system of CryptoGuards by using the Spanning Tree Protocol (STP)
- Passive redundancy system of CryptoGuards
- Geo-redundancy to support the configuration of the security system from different SMS locations and to manage the Backup and Restore mechanism from the master to the slave SMS (the replication of the databases will be done by several DBMS mechanisms like Virtual DBA)
Unix based security management
- SUN SunOS (e.g. Solaris 10 up to SMS version 4.10.xx)
- PC Linux, e.g. SUSE Linux Enterprise Server (SLES 11)
- Possibility of secured remote administration
Database Management System (DBMS)
- Access of Perl scripts to DBMS via ODBC
- Job Scheduler
- ASE XP Server
- Virtual DBA
|
|
Enhancing your security management. The centralized security management approach.
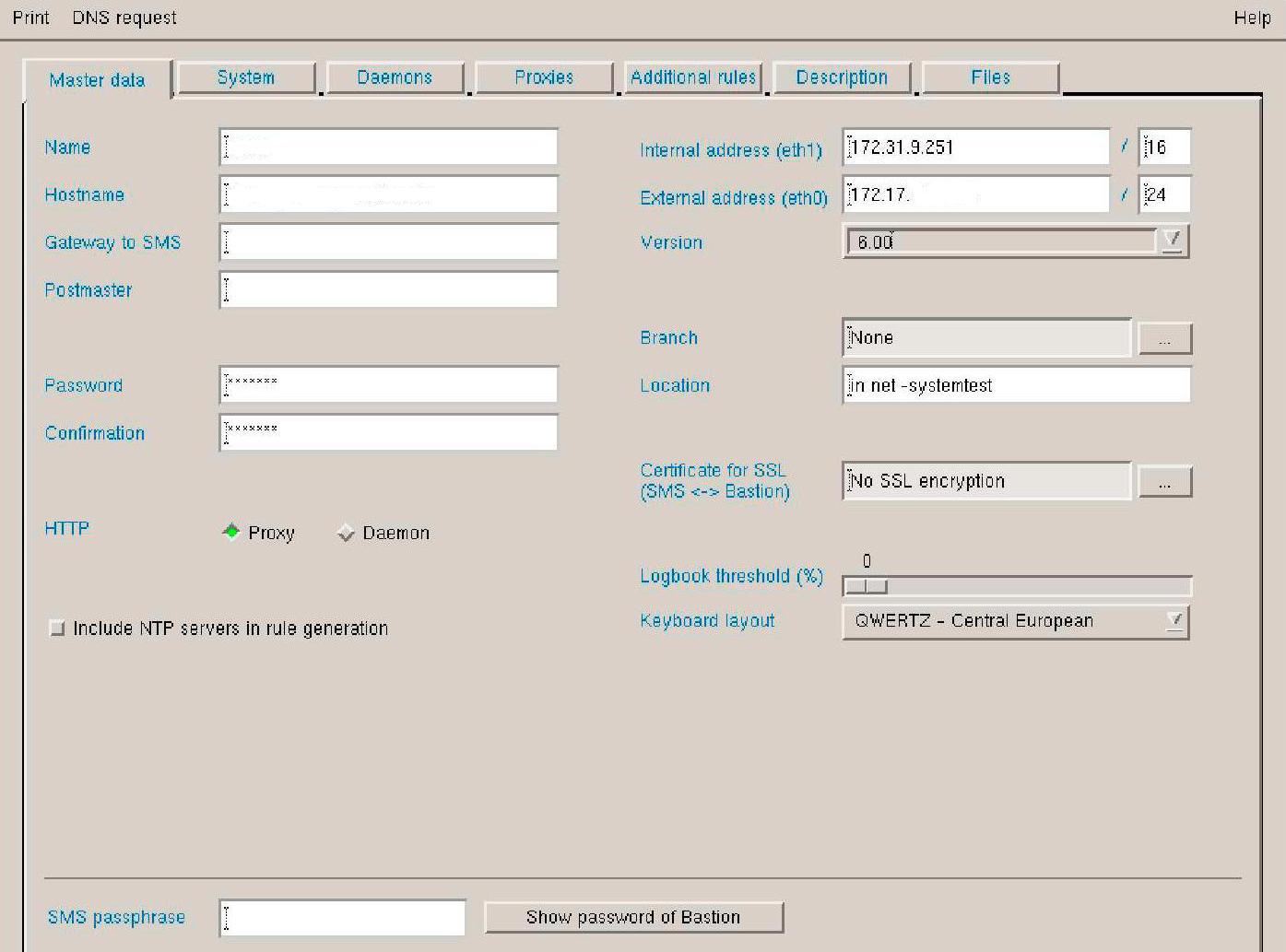
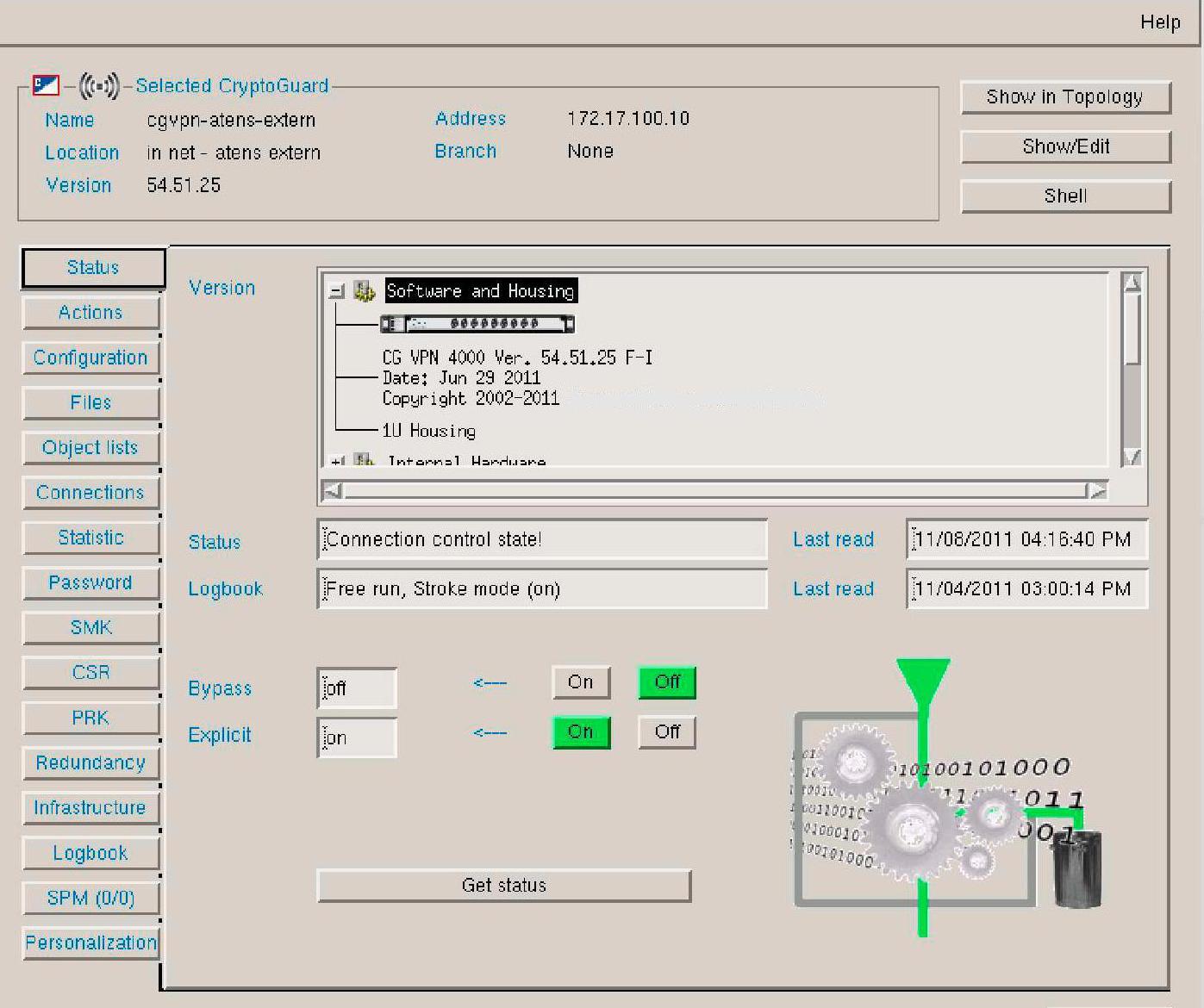
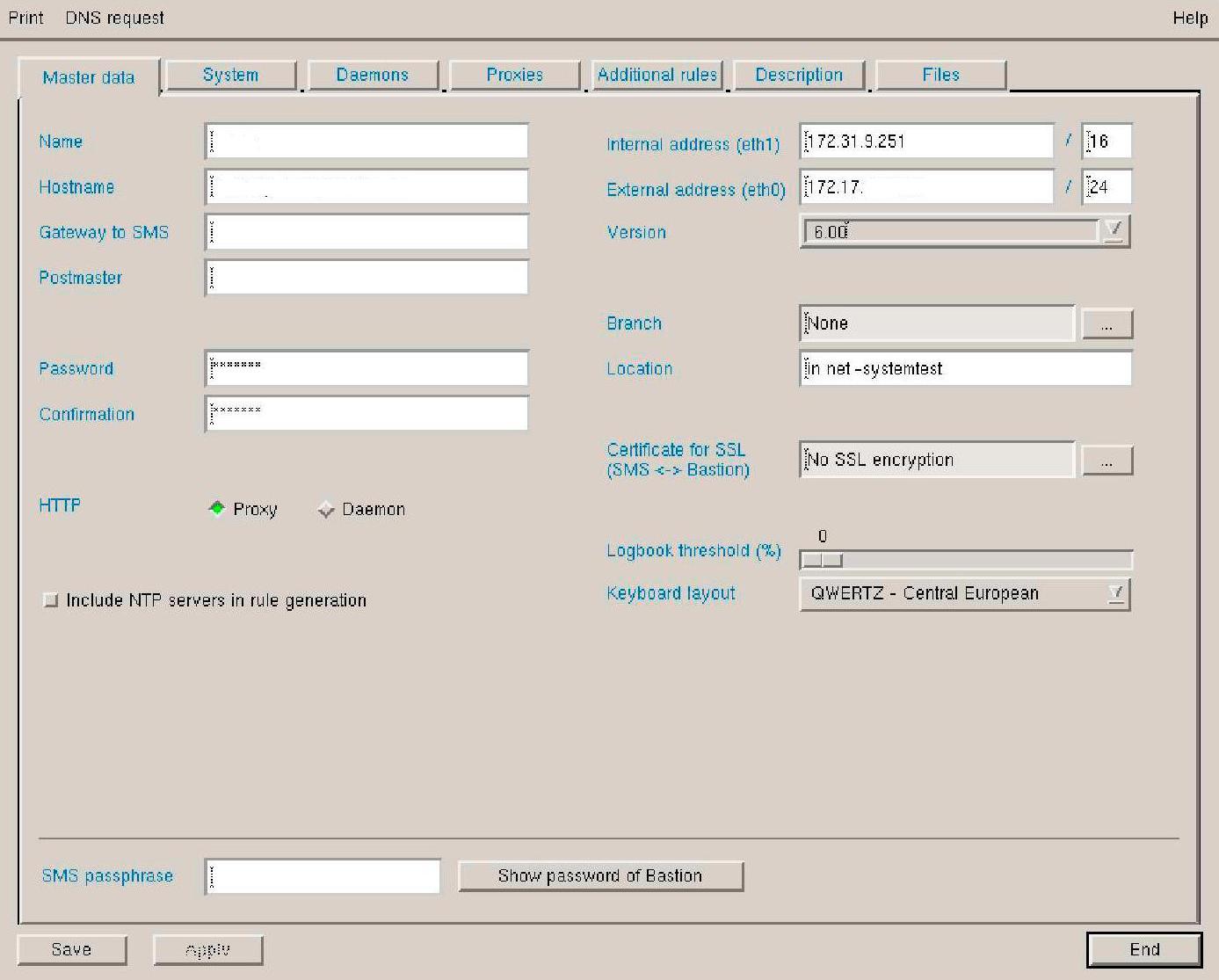
Figure 1 and Figure 2 show examples for the security devices YES Secure CryptoGuard VPN and YES Secure CryptoBastion, respectively.
|
|
|
|
|
|
 |
|
Figure 2.
|
|
|
|
|
|
Key features and benefits of the Security Management Station
|
|
|
|
The network information stored within the SMS is used to display the network topology in a graphical form. This display immediately gives an overview of the network topology and the corporate security manager can use it as a powerful tool for the security administration. He can define secure connections independently of the network environment, using only the end-to-end communication devices.
To expand the security philosophy of the SMS to the users, the concept of a user role is integrated. The security administrator can define different roles for the SMS users, e.g., editor or auditor. Each role is allowed to carry out a defined set of functions. These functional groups also have to be defined by the corporate security manager. Using the role mechanism, he can define, e.g., an editor role which is allowed to enter and store the new network components, their parameters and nothing more. The auditing of these new network components and the definition of their connections can be carried out by a user in a different role, e.g. the security supervisor.
In connection with the security alerts generated by the CryptoGuard VPN devices, the security administrator is informed in real time about violations of his security policy. Companies should always see their security management systems in combination with a network management system; in the last instance such security devices are simply another kind of network device. The SMS, e.g., has the ability to forward security alerts as SNMP traps to a network management station. If the corporate security manager wants to perform a later offline analysis, he can have a look at the security alerts, received from the CryptoGuard VPN devices, which are collected by the SMS and stored in the security alert logbook database.
The corporate security manager can set up a logbook database according to his preferences and requirements. The SMS supports different kinds of logbook databases. There are logbook databases for the CryptoGuard VPN security alerts, for the CryptoGuard VPN security records and for all user activities at the SMS. If the corporate security manager wants to analyze these logbook databases, a detailed history of all activities and security-relevant events in the CryptoGuard VPN security system is possible.
|
|
|
|
Listing of the features and benefits that the SMS offers:
Easy integration into existing network topology
=> CG VPN black box principle
=> SMS integration as a single network component
Backup/Restore mechanism
=> The Backup includes the configuration data of the whole security system
Secured communication between SMS and security components
=> Proprietary authentication protocol based on ITSEC/E3 high certified method
=> Customer specific S-Boxes are loadable
Downward compatible to the beginning
=> Reliable compatibility to CryptoGuards and CryptoBastions of the first generation with a history of about 10 years
Easy definition of secured connections
=> After creation of topology no knowledge of security components necessary
=> Just connection endpoints and security policy necessary
=> Support of templates by using service/protocol/time profiles to simplify the creation of the security policy
=> Simple method of enabling/disabling of connections and protocol profiles
=> As connection mode the proprietary CG VPN mode and IPsec are available
=> Inter-domain communication by using shared key material
=> Automatic generation of configuration files for
CryptoGuards and CryptoBastions
=> According to the proprietary VPN security policy:
All is forbidden except for the explicitly allowed !
Connections
Logging functionality
=> Logging of tasks performed at SMS (functions, errors, login/logout) as preservation of evidence
Excellent key management
=> Automatic generation of connection key files used by CryptoGuards
=> Exchange of connection keys: Beside the key management mode IKEvl also IKEv2 is supported within IPsec
=> Beside the authentication method RSA also ECDSA (Elliptic Curve Digital Signature Algorithm) is supported within IPsec and IKEv2 o Generation of CG VPN Mode keys ((A)DES, 3DES, AES)
=> Generation of IPsec keys (MD5, SHA-1, DES, 3DES, BLOWFISH, CAST-128, AES, ...) RA/CA/PKI included to generate X509v3 certificates e.g. for using in IPsec connections with RSA signatures as authentication method o PKI: Beside RSA also ECDSA certificates are supported o Support of proprietary elliptical curves (EC) o Distribution of the CRL to several LDAP servers o Mark CA certificates as "Trusted", "Not trusted" and "OCSP" Mark certificates near the expiration date o Import of PKCS#12 (Certificate and Private Key container)
=> Smartcard functionality
Centralized security management
=> Centralized point of security management and single point of trust
=> Automatically and centralized configuration of CryptoGuards and CryptoBastions
=> According to the Compumatica VPN security policy: Managing CryptoGuards and CryptoWalls are managed by the push method
GUI based security management
=> User-friendly design
=> Visualization of network topology
=> Visualization of connections and all the security devices involved
=> Powerful search functionality by user defined criteria
=> Multi language support: Currently English and German are available
=> Print functionality
=> HTML based Online Help
SMS owned user access control and role administration
=> Application based user access control
=> Administration of organizational units
=> User roles to split responsibilities
Centralized and user-friendly management of CryptoGuards
=> Configuration by means of dividing generation, transmission and activation of configuration files
=> Certificate Signing Request (CSR). CRL (Certificate Revocation List) and OCSP (Online Certificate Status Protocol) support concerning certificate validation within IPsec
=> Perform Integrity check
=> Retrieving and visualization of statistic information
=> View SA list in case of IPsec
=> Perform Selftest
=> Get Log book
=> Exchange of connection keys: Beside the key management mode IKEvl also IKEv2 is supported within IPsec
=> Software upload
=> White list of version check concerning software upload
=> Import/Export of certificates
Centralized and user-friendly management of CryptoBastions
=> Configuration (General, Proxies, ...) by means of dividing generation and transmission of configuration files
=> Perform Integrity check
=> Select operation mode (Runlevel)
=> Get Log book
=> Retrieving and visualization of statistic information
Centralized and user-friendly administration of network components
=> Single network component, Server, IPsec Client, network
=> Import/Export of network components
Alert functionality
=> Reception of spontaneous messages of CryptoGuards and CryptoWalls and storage in database
=> Forwarding of spontaneous messages of CryptoGuards and CryptoWalls as SNMP-Trap, E-Mail or GSM-SMS
SNMP interface
=> SMS acts as SNMP proxy agent
=> Support of SNMPvS
=> SNMP-Trap. SNMP-Get (Status, Selftest, Statistic, Ping (Echo Request), Version, ...)
=> MIB available
• Administration of batch orders
=> CryptoGuard: Exchange of connection keys : Beside the key management mode IKEvl also IKEv2 is supported within IPsec o Time synchronization between SMS and CryptoGuard o Software upload o Get Log book
=> CryptoBastion: Get Log book o Integrity check o System: Backup
Redundancy mechanism
=> Active redundancy system of CryptoGuards by using the Spanning Tree Protocol (STP)
=> Passive redundancy system of CryptoGuards
=> Geo-Redundancy
Unix based security management
=> SUN SunOS (e.g. Solaris 1O up to SMS version 5.OO.xx)
=> PC Linux (e.g. SuSE 9.S)
=> Possibility of secured remote administration
Database Management System (DBMS)
=> Access of Perl scripts to DBMS via ODBC
=> Job Scheduler
=> ASE XP Server
=> Virtual DBA: The virtual DBA includes database maintenance tasks that are essential concerning database performance and data security.
Using ASE Job Scheduler and ASE XP Server (extended procedures) the virtual DBA supports amongst others the feature Geo-redundancy: If one or more slave SMS exist, the dumps are replicated and loaded onto the slave SMS; this is one more step to improve database security.
|
|
|
|
Graphical Presentation
Network Overview - Moveable Reference Point
|
|
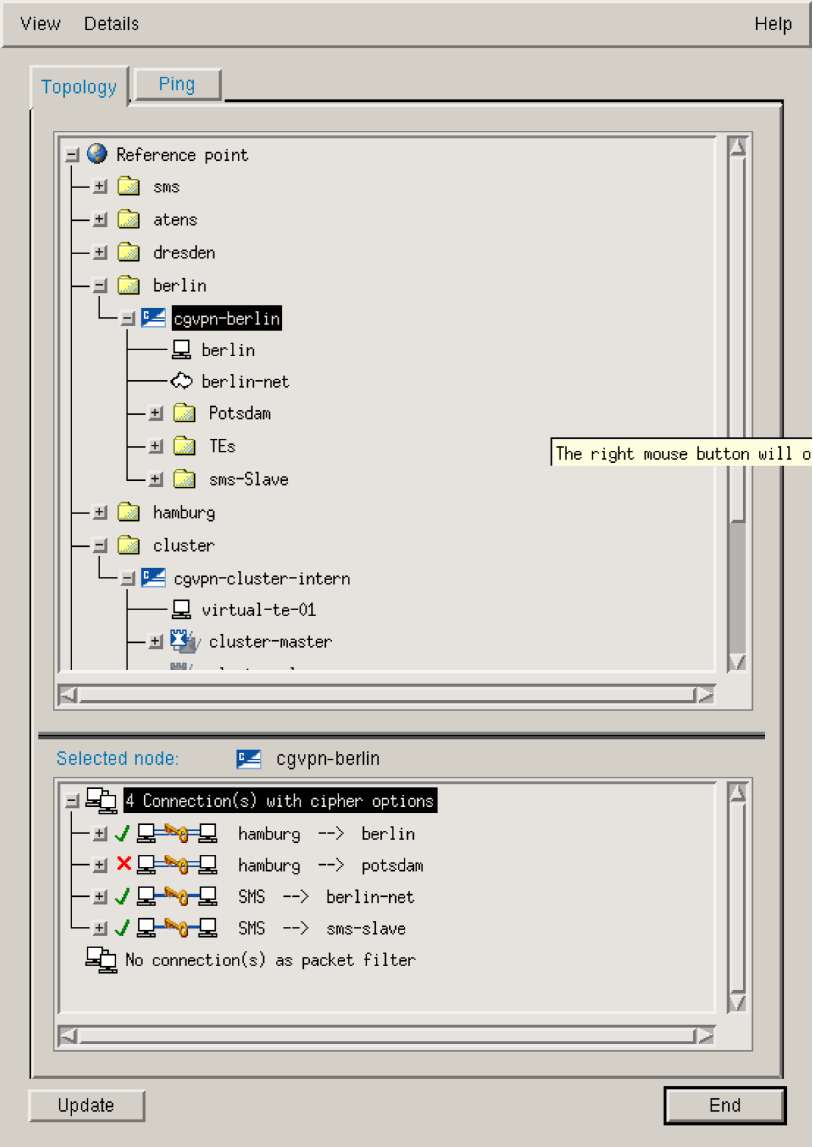
The graphical presentation of a network topology is the heart of the SMS. All relevant network and security components are displayed. This allows obtaining a quick overview of the network and security topology. The reference point of the topology is moveable and can be set at any point in the network. The network topology can therefore be seen from different points of view, depending on which security structure the corporate security manager needs.
Figure 3 is an example for a graphical presentation of a headquarters with two branch offices, all communicating via the internet. The reference point of the topology is the "Internet". The headquarters is connected to the "Internet" via the CryptoGuard VPN device "Internet-Gateway". The two branch offices are connected to the "Internet" via the CryptoGuard VPN devices "Site-A-Gateway" and "Site-B-Gateway".
|
|
|
|
 |
|
ROLE MANAGEMENT
As mentioned earlier, the corporate security manager is able to define different users at the SMS. For each SMS user he has to define a role. When installing the SMS five roles already have been predefined:
- SMS Administrator
- SMS Auditor
- SMS Editor
- SMS Observer
- SMS Operator
The corporate security manager can extend these roles or develop new roles according to his requirements.
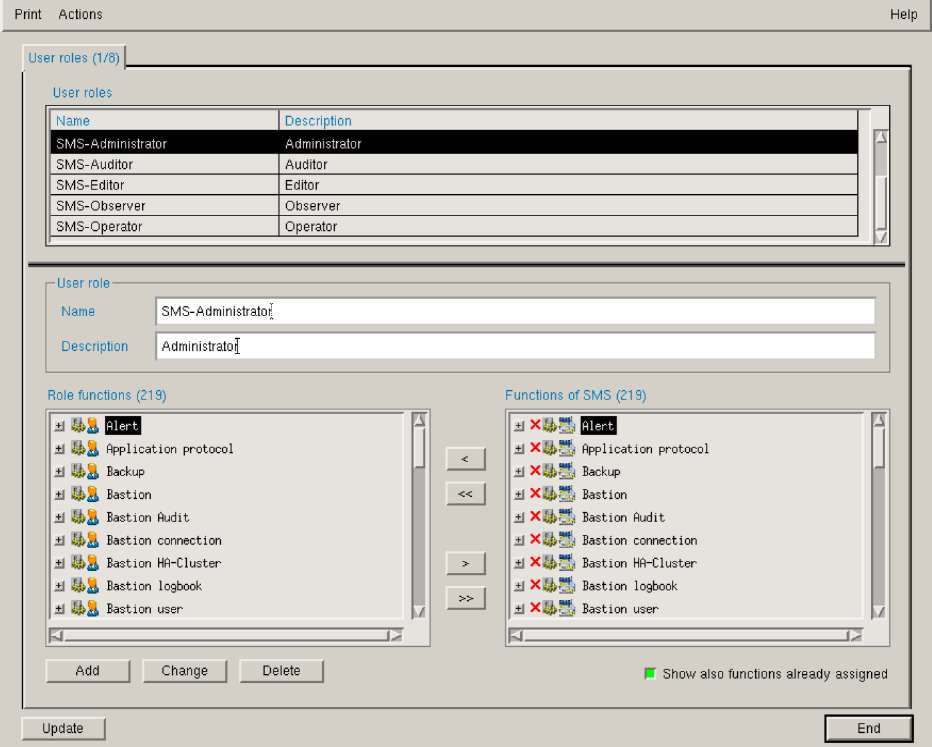
The role definition consists of a name and an assigned set of functions permitted the role. There is one SMS user, however, who needs no role definition: the SMS system administrator. He is comparable to a UNIX "root" account. The system administrator must define the roles and is able to assign any functionality to a role. It is also possible for him to define a role equal to his own, i.e., to define an additional "system administrator" role. Since this role is very powerful it should be protected by a password. Figure 4 shows the definition of a new role.
|
|
 |
|
Figure 4
This mechanism offers many possibilities. One example of what can be realized with the role mechanism is the "four eyes principle". Two roles are defined. The first is allowed to define the data, e.g. the security policy, the second is allowed to activate this data. Thus both roles (four eyes) are needed to define and activate a new security policy for the company's communication.
|
|
|
|
Organizational Units
Organizational units will help to define the independent logical security units within the SMS and are a main part of the central, structured security approach. They can be defined for all types of organizational units, e.g. headquarters, financial departments or branch offices. All components of a defined area will be assigned to a well-defined branch.
Organizational units appear to the user as independent security areas. Different units are only connected to each other if the administrator defines interfaces between them. Thus each unit can be seen as an individual and independent logical security system.
Easy Integration
Easy Integration into Existing Network
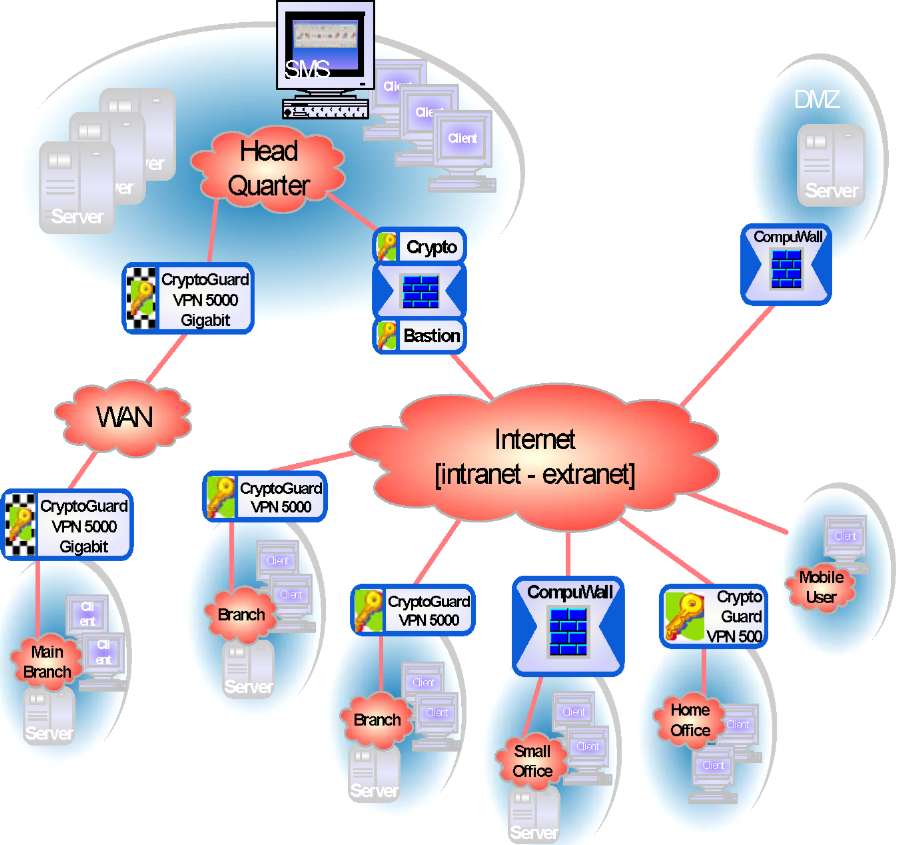
Independent of the already existing hardware the corporate security manager can integrate the SMS into a network as easily as any other workstation. The installation location is independent of the other security components, e.g., CryptoGuard VPN devices. Figure 5 shows a network after integration of the SMS and several CryptoGuard VPN devices.
|
|
 |
|
Figure 5
The communication between the SMS and the CryptoGuard VPN devices (and also, if installed in the network, the CryptoBastion) is secured by strong authentication and encryption, and is independent of the secure communication between the CryptoGuard VPN devices.
|
|
|
|
CONNECTIONS INDEPENDENT OF SECURITY COMPONENTS
|
|
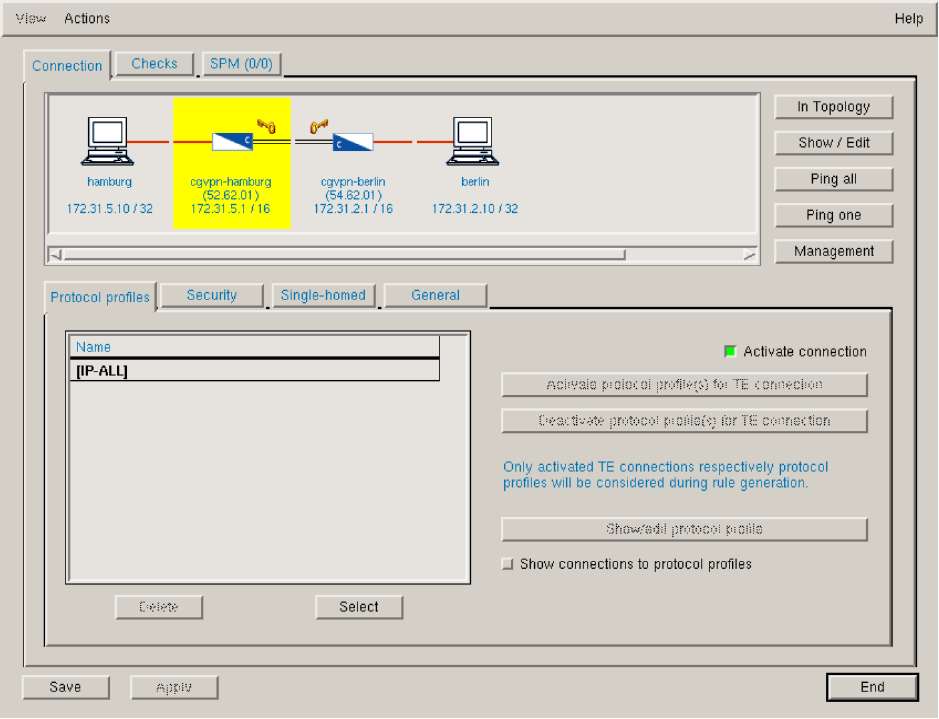
The definition of the security policy entity for the communication between insecure network components (e.g., workstations, hosts or networks) is independent of the network security components involved (e.g., CryptoGuard VPN devices). The SMS automatically checks the security policy and discovers possible inconsistencies. The corporate security manager only has to define the end points of the communication (e.g., 'Clients from France' and 'Important DB Server') and the security policy for the communication between these points (e.g., only allow encrypted HTTP and SQL traffic). The SMS generates from this information the security policy rules for all involved security components (e.g. CryptoGuard VPN devices). Figure 6 shows an example for the definition of such a security policy entity.
|
|
 |
|
Nodes and Networks as Objects
Consistent with the high-level approach to central security management, one thing that must be done is to define a model of the network components (nodes and networks) within the SMS. The SMS handles these network components as objects with attributes. Later, only these objects will be used to define the security policy (e.g., an encrypted connection between net x and node a). Node objects can as well represent individual devices as entire networks. Using the object mechanism, the corporate security manager can integrate large numbers of nodes into one network object to simplify the security structure. Figure 7 shows a list of network and node objects with definitions and notes.
|
|
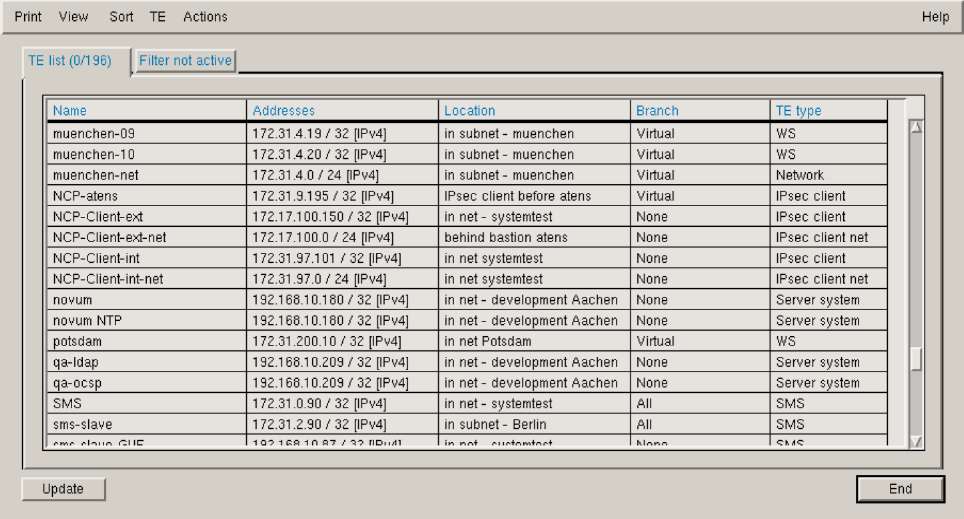 |
|
Protocol Profiles
The corporate security manager can define the security policy (involving, e.g., the allowed protocols and a specification of encrypted or plain connections) with "Protocol Profiles" as shown in Figure 6. Protocol profiles are an additional mechanism to assist in the high-level view approach. With protocol profiles the corporate security manager is able to see more at the application than at the protocol level (e.g., the profile "Config Bastion" in Figure 8 collects each protocol needed to configure a CryptoBastion). The security policy definition can use these profiles to set up all needed communications between the SMS and a CryptoBastion.
|
|
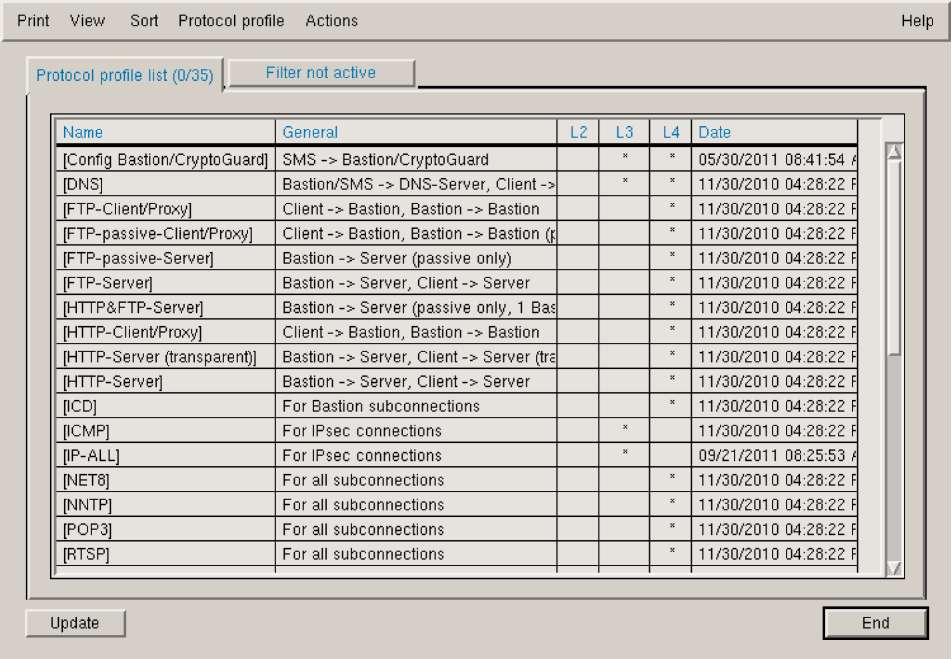 |
|
Figure 8 |
|
Key Management
Key management is highly important within a security system. A strong key management represents a major aspect for each security system. This was kept in mind during the design of the key management for the CryptoGuard VPN system. A PKI (Public Key Infrastructure) represents the whole of all components that are necessary to generate, manage, distribute and revoke digital certificates.
Keys for the entire system are generated and stored on the SMS. The pseudo-random number generator used for key generation and the key storage fulfill high security requirements.
The primary CryptoGuard VPN device keys (the CryptoGuard VPN master keys), which will be used for the later encrypted communication between the SMS and the CryptoGuard VPN device, are transferred during the first contact between the SMS and the CryptoGuard VPN device. The key transfer has to be done in a secure environment, using a serial link between the SMS and the CryptoGuard VPN device. After this step, which is called "personalization" of the CryptoGuard VPN, the SMS and the CryptoGuard VPN device are able to establish a secure session via the network (e.g., Internet).
The corporate security manager can manage the distribution of new keys by the SMS during normal daily business automatically or manually. Automatically means that the SMS changes the keys in a CryptoGuard VPN device at a defined date and time independently of any instructions. The corporate security manager only needs to specify the date, time and CryptoGuard VPN devices. Manually means that he has to start the key change for each CryptoGuard VPN device on his own.
The newest version of the SMS supports as well smartcard functionality. This means an easy and comfortable way for the user to personalize on the SMS.
Logbooks
The SMS supports a management activity logbook and two security device logbooks.
Each function activated at the SMS generates a logbook entry at the management activity logbook. The management activity logbook shows which user activated which functionality, and when. It logs the history of the entire security system for the later analysis.
The corporate security manager can configure the CryptoGuard VPN devices to send security alerts in real time to the SMS, which receives them, displays a message on the screen, and stores the security alert in the security alert logbook for later analysis. He can also configure the SMS to additionally send an SNMP trap to a defined network management system. Individual security alerts are stored for each CryptoGuard VPN device.
The second security device logbook is the security record logbook. Each CryptoGuard VPN device has its own logbook, storing security records defined by the SMS. As the logbook size in the CryptoGuard VPN devices is limited, the corporate security manager should save the security records periodically to external media. This is done by transferring the security records from the CryptoGuard VPN to the SMS. On the SMS, the received security records are stored in the security record logbook. The security records are stored individually for each CryptoGuard VPN device.
The corporate security manager can export all logbook entries in standard export format for use with third party analysis tools and is thus able to keep the whole offline analysis as flexible as possible.
BATCH JOBS
If the corporate security manager has a great work load and e.g. wants to start many activities at a defined date and time, batch jobs are an instrument to distribute the work load,
distributing new connection keys to all CryptoGuard VPN devices on Friday at 10:00 PM and activating these keys on Saturday at 1:00 A.M. The corporate security manager can automate such activities using batch jobs. He only has to define them once and they will be carried out at the defined date/time.
Additional examples for batch jobs are:
- periodic reading of the CryptoGuard VPN logbooks
- periodic backups of the SMS database
- automatic distribution of software updates.
Redundancy
Since the SMS itself is the central possibility to manage the CryptoGuard VPN security system it is advisable to have a redundant SMS for large networks requiring high availability.
CryptoGuard VPN, CryptoGuard VPN Client and CryptoBastion have redundancy mechanisms with support of third party components independent of that of the SMS.
It is possible to integrate two ore more devices in parallel into one system to increase the availability of the network. The route is checked regularly; this allows to recognize if an active CryptoGuard VPN device (called 'Master') failed and if so, to remove it from the system. In that case, a second by then passive CryptoGuard VPN of the redundancy system (called 'Slave') becomes the active one.
New feature: Geo-Redundancy to support the configuration of the security system from different SMS locations and to manage the Backup and Restore mechanism from the master to the slave SMS (the replication of the databases will be done by several DBMS mechanisms like Virtual DBA).
Remote administration
The corporate security manager may have a need for managing the SMS remotely; for this remote management functionality is included.
Remote management is realized using the standard X-Window system of the SMS operating system by tunneling it in an encrypted Secure Shell (SSH) session to a remote client.
Conclusion
In times of more and more severe attacks on computers and computer networks managers should especially keep in mind the damages emerging from these attacks and consequently attach great importance to network security. In order to protect their confidential data many organizations are seeking for a comprehensive, reliable and easy to handle opportunity.
For companies that have a great need for a security management enabling a centralized and comfortable administration the Security Management Station solution provided by YES Secure network turns out to be an ideal way to manage their security concerns. Its uncomplicated integration as well as its numerous functionalities offer a perfect base for the setup of a stable and reliable corporate safety policy.
For information concerning the further parts of the YES Secure Network system contact us now.
|
|
|
|
Technical Data Security Management Station (v.5.40.xx)
Operating Systems: SLES 11 SP1 or higher (32 bit)
Database: Linux: Sybase Database Version 15.0.3 EBF 17776 ESD#4
Platforms: Linux: Intel hardware (64 bit) CPU: Quad Core
Abbreviations
CG VPN : CryptoGuard VPN: product to secure network communication.
IETF: Internet Engineering Task Force: Organization, which defines the standards, used in the Internet.
IKE : Internet Key Exchange: A protocol defining how to exchange keys for IPsec communications. Defined in RFC 2409.
IPsec : IP security: A standard which defines various security services for traffic at the IP layer. Defined in RFC 24012411.
KGL : same as KGLAN
KGLAN : KryptoGuard LAN: former name of the CryptoGuard VPN product.
LAN : Local Area Network: Any physical network technology that spans short distances (up to a few thousand meters).
SLES : SuSE Linux Enterprise Server
SMS : Security Management Station: former name of the CryptoGuard Security Management CGCM.
VPN : Virtual Private Network: Synonym for doing network communication over a public network in an encrypted way, so that only participants that share the necessary keys are able to communicate.
|
|
|
|
Back to YES Secure Network |
|
|
|
|
|
|
|
|
|
|
|